Mobile app security is the extent of protection that mobile device applications (apps) have from malware and the activities of crackers.
Crackers can reverse-engineer the Android application source code and access the contents of the package. All the drawable, sensitive string constants in code (application IDs, private web service URLs) and the business-critical logic are revealed and can be manipulated further.
Nowadays there is no need to know the entire reverse engineering process all are available in online itself. For this process you need the APK file, you can get the APK file from here. Now you need to decompile it using this site. Here you just upload the APK and then you can get the source code of the application.
If the developer not aware of Proguard you can get their code within 10 mins.
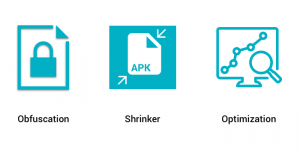
Enter Proguard. Proguard makes your APK file as small as possible, it removes unused code and resources in your release build.
It optimises the bytecode, removes unused code instructions, and obfuscates the remaining classes, fields, and methods with short names. The obfuscated code makes your APK difficult to reverse engineer, which is especially valuable when your app uses security-sensitive features.
Uses of ProGuard :
- Creating more compact code, for smaller code archives, faster transfer across networks, faster loading, and smaller memory footprints.
- Making programs and libraries harder to reverse-engineer.
- Listing unused code, so it can be removed from the source code.
For adding ProGuard rules you need to do the following changes to the appropriate build type in your build.gradle file.
| buildTypes | |
| { | |
| release | |
| { | |
| shrinkResources true | |
| minifyEnabled true | |
| proguardFiles getDefaultProguardFile(‘proguard-android.txt’), ‘proguard-rules.pro’ | |
| } | |
| } |
shrinkResources true : To enable resource shrinking.
minifyEnabled true : To enable code shrinking.
The proguardFiles property defines the ProGuard rules:
The getDefaultProguardFile(‘proguard-android.txt’) method gets the default ProGuard settings from the Android SDK tools/proguard/ folder.
The proguard-rules.pro file is where you can add custom ProGuard rules. By default, this file is located at the root of the module.
Add the following rules into your proguard-rules.pro file
| // Basic proguard rules | |
| -optimizations !code/simplification/arithmetic | |
| -keepattributes <em>Annotation</em> | |
| -keepattributes InnerClasses | |
| -keepattributes EnclosingMethod | |
| -keep class *<em>.R$</em> | |
| -dontskipnonpubliclibraryclasses | |
| -forceprocessing | |
| -optimizationpasses 5 | |
| -overloadaggressively | |
| // Removing logging code | |
| -assumenosideeffects class android.util.Log { | |
| public static *** d(…); | |
| public static *** v(…); | |
| public static *** i(…); | |
| public static *** w(…); | |
| public static *** e(…); | |
| } | |
| // The -dontwarn option tells ProGuard not to complain about some artefacts in the Scala runtime | |
| -dontwarn android.support.** | |
| -dontwarn android.app.Notification | |
| -dontwarn org.apache.log4j.** | |
| -dontwarn com.google.common.** |
If your Android application includes any library(jar,dependency), you also need a few lines of configuration. For example processing Crashlytics code as given below
| -keep class com.crashlytics.** { *; } | |
| -keep class com.crashlytics.android.** | |
| -keepattributes SourceFile,LineNumberTable |
You can find more basic proguard rules in the official docs, also find commonly used rules for library files in this Github repo.
Sometimes generating signed APK using the wizard (Build – Generate Signed APK) is not implementing the proguard rules.You can either build the release APK from the command line with the command:
| ./gradlew assembleRelease |
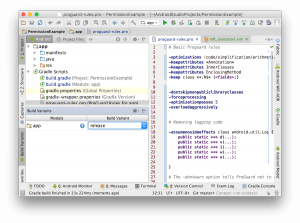
or you can choose the release variant from the Build Variants view and build it from the GUI:
Jaison Fernando
Latest posts by Jaison Fernando (see all)
- Phone number auth using Firebase Authentication SDK - March 20, 2020
- Password-less email auth using Firebase Authentication SDK - March 9, 2020
- How to use SharedPreferences API in Android? - February 10, 2020